The recent attack on Kronos proves that organizations need to ransomware-proof their backups. Kronos is a Human Resources and Workforce automation software provider. The company admits to becoming aware of a cyber-attack on December 11th and, as of January 12th, is not yet claiming complete restoration of their customer’s data.

While there are few details of the attack, available information suggests that the attacker started with infiltration of their backup software and then planted a ransomware trigger file to encrypt data throughout the organization. The organization could not access its backups to recover from the attack on the rest of the environment. The result is, at this point, a month-long recovery process.
IT should take three lessons away from this attack:
- Backup Data must be protected from cyber-attack
- Backup metadata must also be protected from cyber-attack
- You need a “clean” recovery target to act as standby storage after a cyber-attack
These lessons are new and should be considered enhancements to the steps we outlined in our white paper “A Three-Step Ransomware Recovery Guide.”
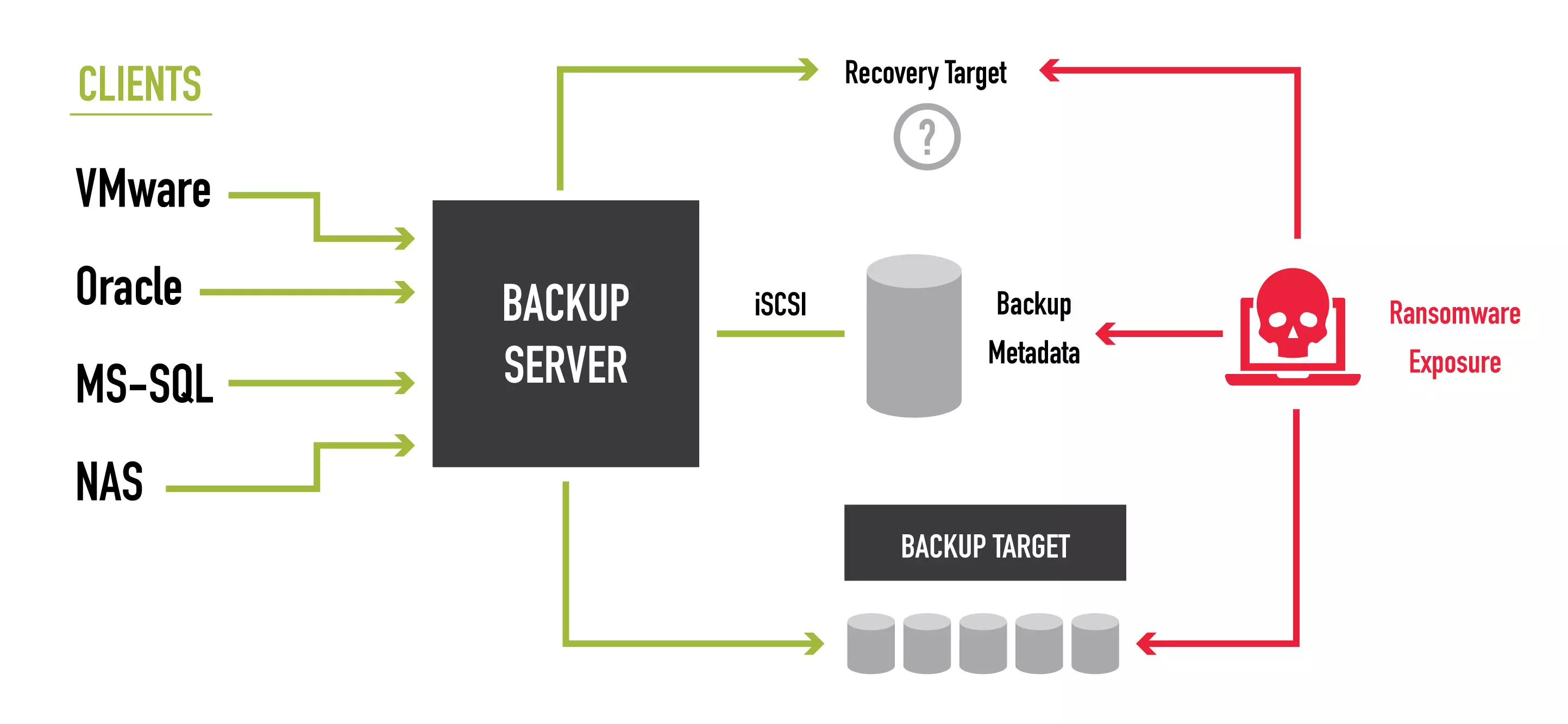
Ransomware-Proof Backup Data
The first lesson is that backup data itself must be immutable so that a ransomware attack can’t encrypt the same data you intend to use for recovery. The problem is, backup data does need to change, especially if you are using block-level incremental (BLI) or change-block tracking (CBT) backup techniques. The answer is to use immutable snapshots, capturing every version of every backup job and securing from a potential breach while not impacting backup ingest performance. StorONE’s S1:Backup provides complete immutability of every backup job across all protocols, and media types with infinite retention, without impacting performance.
Ransomware-Proof Backup Metadata
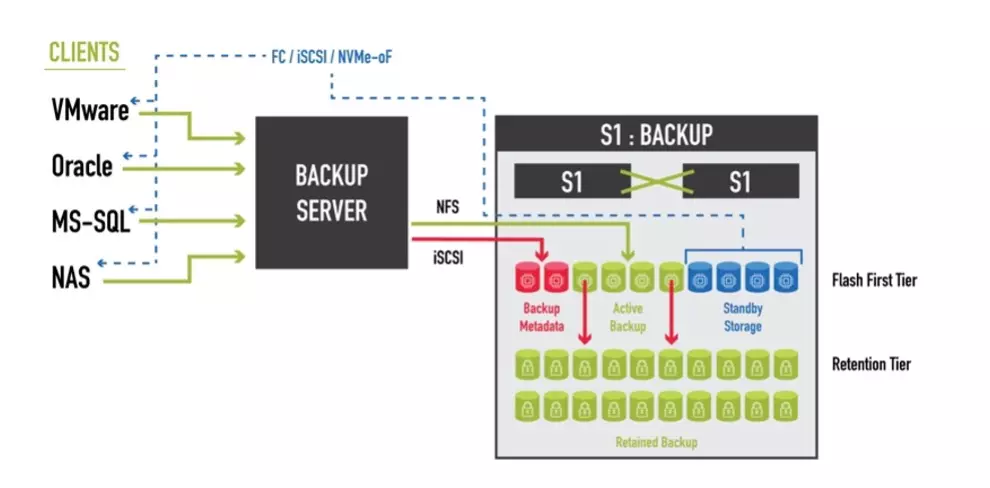
Backup-server software is a robust, IO demanding application. It also creates a lot of metadata (data about the protected data). Backup software stores this metadata in a series of index or database files. It enables the backup administrator to interface with the backup devices, scan for a specific version of files, and manage data retention. The performance demands of the backup software mean that IT needs to store metadata separately from the backup storage target, typically on production storage or on an array dedicated to the backup server software, further fragmenting the storage infrastructure.
If this data is somehow compromised, recovery may be impossible or, at a minimum, very time-consuming. The Kronos attack is proof that bad actors are targeting backup data in parallel to their attack on the rest of your environment. Protecting backup metadata is critical to recovery.
Again, the answer is storing this data in an immutable state, but, even more so than the backup storage target, this data needs to change, and it needs to be on storage that is very responsive to high-IO demands. Most production storage systems don’t provide immutability. Except for StorONE’s S1:Backup, most backup storage targets can’t meet backup software metadata’s IO demands.
S1:Backup solution is built on the StorONE Enterprise Storage Platform. That means that while it is priced competitively against typical backup storage targets, it also provides the performance and availability the backup application requires from a volume to store its metadata. That volume can also leverage our immutable snapshot technology to protect the backup software’s metadata from attack.
Ransomware-Proof Standby Storage
Another challenge that IT faces when recovering from a ransomware attack is deciding if it is safe to recover to production storage. IT needs to ensure that the ransomware trigger file and its replicants are removed from the environment. If one copy goes unnoticed, the organization may be in the same situation a few hours after recovery is complete.
In a perfect world, you’d have an exact copy of your current storage system, powered off and disconnected from the network. Few, if any, organizations can afford this level of redundancy and protection. Also, even this extreme level of redundancy won’t protect from the new system being compromised if the ransomware isn’t entirely eradicated.
StorONE’s S1:Backup solution is also Standby Storage, which means that it leverages our Enterprise Storage Platform to deliver production class performance, availability, data protection, and data integrity. The system is not sitting idle, waiting for a ransomware attack. It is working as backup storage and storing production backup metadata. All data is immutably protected via our snapshot technology.
IT can leverage the backup-server software’s instant recovery features during a ransomware recovery or recover directly to volumes on the S1:Backup infrastructure. IT can assure the organization that these volumes are “clean.” IT can also leverage the same immutable snapshot technology to protect and quickly recover these new production volumes if they miss one of the malware replicants.
To learn more about how StorONE’s S1:Backup and Standby storage can ensure complete and rapid ransomware recovery, register for our live webinar on January 27th at 11:00 am ET. We will send you an advanced copy of our latest white paper, “What is Standby Storage?”